Cloud Security: An Introduction
The cloud. It's the greatest trend in physical security right now, but there’s still some scepticism around its use. Migration. Cybersecurity. Device compatibility. Despite trusting the cloud in all forms in our personal lives, businesses are still relying on outdated legacy technology to keep them safe - ignoring the advantages that cloud based security has to offer them.
If you’re serious about keeping your business safe, or you have a business that is scaling its operations, you need to look at a cloud based solution. In this guide, we’ll cover everything you need to know about cloud security systems. We'll explore what they are and how they can play a role in the running and safety of your business.

The Ultimate Cloud Security Guide
.png?width=1900&height=519&name=Cloud%20Security%20An%20Introduction%20(2).png)
What Are Cloud Based Security Systems?
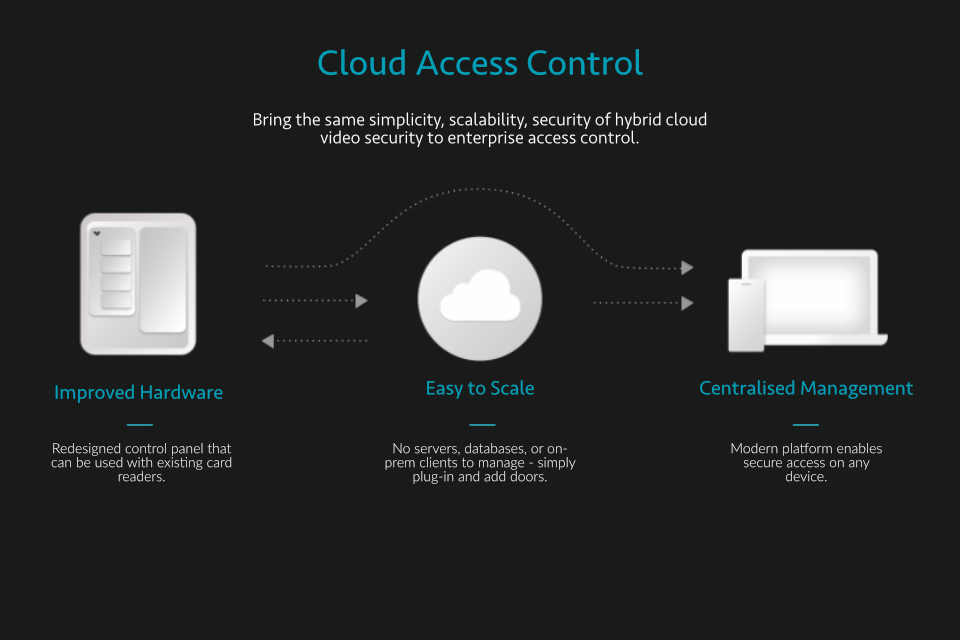
A cloud security system is a network of physical and digital security devices that are connected through the internet with data, footage and archives being stored in the cloud - rather than on-premise. They're designed to get rid of the management, security and hardware limitations associated with the physical security devices that business owners keep in their buildings - with a number of key additional perks.
Why Choose Cloud Security?
Cloud security ties all of your devices into a single interface, meaning you don’t need multiple apps and software to manage various systems. This reduces the amount of training staff need and means integration between the different disciplines is reliable, supported by the single vendor solution. This technology is able to access every part of your security system for review and control from an internet connected device, letting you check your cameras out of hours, monitor staff sign-in, give visitor/contractor access with two clicks or even disarm/arm your intruder alarm on-the-go.
Traditionally, security devices and applications have relied on hardware stored on site, which offer limited access and little-to-no remote accessibility. Cloud security systems do away with this old tech. The cameras and access controllers connect directly with the cloud or data centres through the internet. An NVR is limited by the number of output ports or the power required to store and process your CCTV images. With cloud the system scales up or down with your needs. If you have a hardware failure for example, unexpected repair bills can run into thousands for replacement NVRs or servers. This is also a single point of failure for your system. With cloud systems you are often guaranteed 99.9% uptime or better and there are no unexpected repair costs as you pay for the service monthly. The cloud essentially gives the user all the benefits of an enterprise level connected security system, without requiring complicated VPNs or port forwarding.
Cloud based security is also highly-secure in terms of data security. Every business owner has a duty to protect the privacy of their staff and customers under GDPR and data protection law. With data being stored in the cloud, with password-gated control and multi-factor logins, operators have that extra peace of mind that their data is hidden from prying eyes. Read more about the reasons to upgrade to cloud.
.png)
What Is Cloud CCTV?
Cloud CCTV refers to video surveillance systems that store CCTV footage in an off-site secure data centre or on the camera with a direct connection to the cloud, rather than storing footage on-premise with a server or NVR. This means the system is infinitely scalable as you don’t need to upgrade hardware or add storage as you expand or improve your system. Cloud systems are constantly improving with automatic software and firmware updates, and are far more secure than on-premise internet connected systems.
By storing video data digitally in the cloud, operators can access their systems from any internet-connected device using simple to use, constantly improving user interfaces - without ties to a specific on-site location.
Unlike traditional CCTV, there’s essentially no need for bulky on-premise NVRs, saving costs on expensive physical storage maintenance, power consumption and space, as well as reducing the risks associated with keeping security data on-site (more on that later).
Paired with powerful video analytics like facial recognition and ANPR, cloud CCTV instantly offers a far more reliable, trustworthy and secure option for business owners looking to remodel their security strategy.
Features of Cloud CCTV
Cloud CCTV packages are designed to enable operators to proactively protect their business. Powered with realtime activity alerts, sent straight to the operator’s phone, this technology enables users to act quickly, rather than just reviewing the footage after an event has already happened.
Alerts can be programmed for specific AI-based rules, like a person crossing a perimeter boundary, out-of-hours movement detection or even facial recognition for repeat offenders.
With no DVR or NVR on-site, cloud CCTV also actively prohibits the vast majority of internal crimes as well. Historically, with storage held on-premise, employees have been able to damage on-premise hard drives to remove any evidence of their crimes. With a cloud-based system, this is no longer possible as everything is backed up in the remote server.
For businesses that require multiple log-ins and access to their CCTV system (large scale security and HR teams), operators will be able to monitor audit trailing of changes made in the footage archive. Essentially, if any member of staff tries to tamper with or share surveillance footage, this is automatically recorded on the system.
You can even connect these systems to management systems like Okta or Azure AD to automatically add and remove users to your system as they come and go from your organisation.
By storing recorded data in the cloud, operators gain quick, easy access to their CCTV footage from anywhere with an internet connection. Usually offered as part of a Software as a Service (SaaS) package, all CCTV footage is stored securely, without risks of data being overwritten or corrupted. It also means that if your internet is down or power is off at your property you can still access the archived footage in the cloud, giving you an insight as to what happened before the power outage.
With more sophisticated platforms, users are therefore able to search across their entire archive for specific events or persons of interest with quick, easy and detailed Smart Search features such as date, number plate or even specific clothing colours. Everything your cameras have ever recorded is right there at your fingertips for use as evidence in criminal trials, insurance claims or else.
As a modern IP-based video surveillance solution, cloud CCTV can be enhanced to send notifications for specific triggers on your premises, with intelligent programming to gather data and track every movement made in and around your building.
Typically, these analytics include ANPR recognition, facial recognition for persons of interest and movement detection for out-of-hours alerts or unauthorised staff activity in prohibited areas like a server room.
Video analytics are by no means exclusive to cloud CCTV, but with cloud, you access the latest and greatest AI innovations and algorithm improvements as they happen, without expensive hardware upgrades or replacements. These are simply installed remotely as part of your SaaS subscription. Whereas, at the current rate of innovation, by the time you install a standalone NVR/DVR system, it’s already become outdated.
Aside from the clear security benefits, cloud security can also be used to optimise operations, management and business performance across your premises.
Using video analytics, operators and marketing teams can gain situational insights into key performance areas of their business; count vehicles and people on site, view visual heat maps to understand hot spots and dwell times, or manage occupancy for shift scheduling.
Cloud CCTV users also benefit from specific use-case scenarios where video analytics and proactive alerts can play a role. For example, in warehouses or construction sites, operators can trigger an immediate notification for anyone on site not wearing a Hi-Viz vest or hard hat, offering greater visibility over your operations and accountability should something go wrong.
A major advantage to cloud based CCTV systems is that they’re infinitely scalable and perfect for multi-site application as users aren’t limited by the hardware on site recording. Generally NVR’s come in 4, 8 or 16 channels so you’re often purchasing more than you need up front or limited by the components you choose to install at the time
Operators are able to monitor every single property under their umbrella from one single interface, rather than having a complex VPN system set up for each site. For growing businesses, this is a major bonus. As you expand your portfolio with new locations, adding CCTV becomes a simple plug-and-play process where you can just bolt on additional cameras, storage and resources to your system as you need.
Leveraging the power of cloud control, high-standard cloud CCTV systems update automatically and remotely with 24/7 firmware updates to ensure your cameras are running at peak performance and protected against the latest threats.
From a troubleshooting perspective, problems with a cloud based CCTV system can be dealt with in a way that we’re entirely used to. Like on most SaaS platforms, there’s embedded chat as a support service, meaning users can simply request a ticket for remote maintenance or troubleshooting. Most issues can be resolved remotely, removing the need for costly on-site technician support.
With proactive notifications and live health monitoring, users will also be able to be alerted to any faults that may result in security downtime, like a camera outage or programming error.

An Expert's Guide to Cloud CCTV
Security systems have come a long way since the days of heavily-wired, monochrome cameras and titanic racks of VCRs requiring daily tape changes record footage.

The Best Cloud CCTV Systems for 2024
Cloud based CCTV systems are quickly taking over the security industry. Looking to move your surveillance into the cloud? We've got you covered.

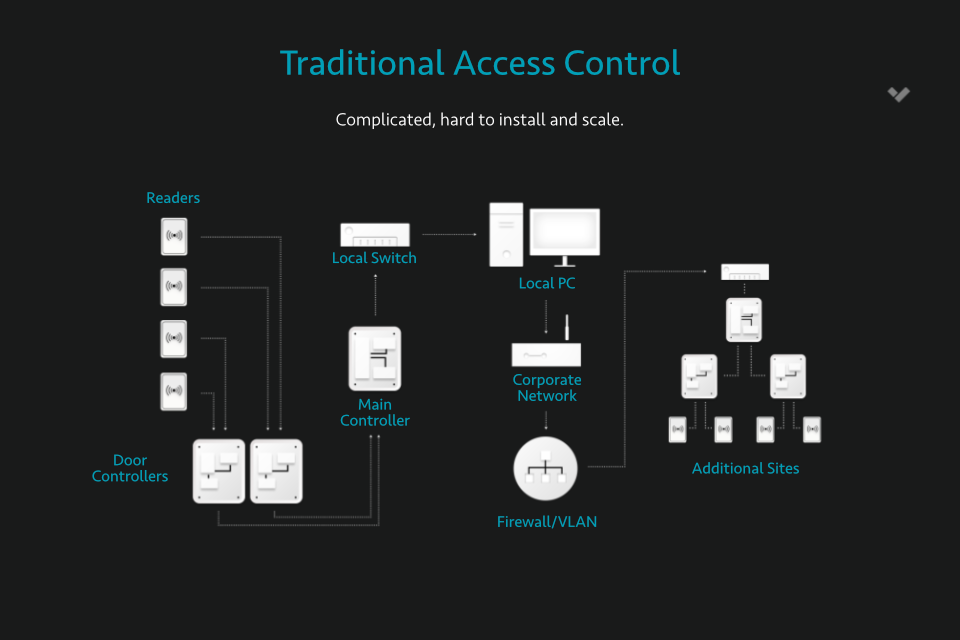
Cloud based access control solves a vast majority of the modern challenges linked with business access. These systems give operators the ability to remotely control and manage all access control doors on their property via an internet-enabled device.
While some traditional access control systems give users the ability to access their interfaces remotely, this can only be done by setting up a virtual private network (VPN). Cloud doesn't require its own private network. Everything from employee credentials to relevant access information is stored entirely digitally, and accessible on authorised smartphones and browsers, making it less vulnerable to corruption or physical damage.
Just imagine if the hard drive storing all of your employee access credentials were to corrupt. You’d have to physically re-enroll every single member of your company. With the cloud hosting the software, this is no longer a concern. Building owners enjoy added convenience, security, removing the expense and hassle of housing rack storage, power and hardware on-site. It’s for this reason that cloud access control is often adopted by businesses with a high number of employees. It offers an efficient means of editing door schedules and distributing access permissions on the go from a single software or device. All from a single software or device. The alternative is revising complicated credentials each time a permission needs changing.
Not only does this add greater simplicity for the end-user, cloud access control also improves and enhances the operation of door, identity and access management control. Access alerts, heatmaps, entry event timelines and occupancy monitoring are all features of most modern cloud systems.

Analytical, Data-Driven Door Control
Remember:
- Full Door Schedule Control.
- Quickly Find & Respond to Access Alerts in Real-Time.
- Detect & Verify People Based on Face ID Data.
Features of Cloud Access Control
With remote monitoring and live access reports, cloud access control systems enable operators to respond to entry threats, tailgating (when integrated with CCTV) or security breaches as they happen. If an unregistered user attempts to gain access to the property, or if a door is being propped open, a signal will be raised and a warning notification issued to the business owner on their remote device.
With dynamic visual reports on access activity stored in an intuitive interface, users can also assess the historical timeline and audit trailing of events from their device, increasing readiness to respond and helping to make more informed decisions on site security.
With access event timelines being stored entirely digitally, cloud access control presents a unique opportunity for businesses to actively monitor the occupancy and capacity of their buildings. From a compliance standpoint, you can pull up a report at the click of a button. This can be used for: emergency roll call, monitoring occupancy, arrival time tracking, unexpected absences and more.
Occupancy monitoring can also be used to proactively monitor capacity in specific zones of your building that require occupancy management such as car parks, staff cafeterias or gyms. In some situations, the readers can even be remotely programmed to automatically deny new entries until capacity falls below a set number.
Using mobile credentials, cloud based access control systems make user setup and distribution simple, accessible and user-friendly. With this technology, there’s no need to print keycards or issue RFID fobs for each and every user added to the database, which can be time-consuming and expensive.
Standard cards and fobs can still be used, but with mobile credentials, operators only need to send a user credential through to their phone, have them download an app, and register for immediate access through bluetooth, Wi-Fi, 4G or the phone’s built-in NFC chip. This makes mobile credentials near impossible to duplicate, clone or forget.
Once logged into the interface on a browser or smartphone, all your credentials, information and access activity is right at your fingertips, even if you have thousands of employees and unique permissions for each.
Through remote access to the credential database, admins are able to issue or edit permissions to users quickly and efficiently. This could be through key fob, biometric access or mobile phone credentials, operators can simply add, edit or assign permissions and have these configured and activated instantly, without needing to be on-site or connected to the local area network (LAN).
A major plus for cloud access control is that it’s endlessly scalable and can grow alongside your business. Using plug-and-play ‘Access Controllers’, users are able to instantly connect new and existing door readers on multiple sites to their cloud system through internet connection, without needing to configure new VPNs, firewalls or additional servers across multiple sites.
This technology also gives business owners the freedom to expand their workforce without hesitation. With a private cloud server, businesses are not being limited to server hardware or storage, meaning cloud access control is infinitely scalable from a credential perspective. You can start with a system holding 50 access credentials and scale up to unlimited without having to replace any onsite hardware.
Cloud based access control can be taken the extra-mile with CCTV integration, giving users 24/7 visual access to their controlled doors. With the right setup, users can arm their access control with facial recognition and visual confirmation of every user that passes through the entrance, backing up the audit trailing with cold, hard video evidence.
Cameras can also be used to proactively detect user tailgating or doors being held open. By intelligently recognising these events using video analytics, the system will alert the admin on their mobile device, allowing them to respond to access alerts safely and proactively.

Best Cloud Access Control Systems
Access control has come a long way since the days of keypads and card readers. Now, businesses across the globe are being accessed with a wide range of different credentials - from mobile phones, to fingerprints and facial recognition.
.png)
What Are Cloud Intruder Alarms?
Cloud based intruder alarms provide businesses with the tools to detect and respond to threats in their buildings as they happen. Linked to a control app on a smart device, cloud alarms connect users straight to their security system. They instantly raise an alert for suspicious activity on the premises, and give users the chance to respond proactively, rather than after the fact.
Using data taken from a range of security devices, like CCTV video intelligence, access control and sensors, cloud alarms identify important events. They provide full visibility over the building as incidents unfold, rapidly alerting ARCs (Alarm Receiving Centres), emergency services and the end-user in real-time.
Paired with a cloud CCTV surveillance system, users get event-based video feeds, triggered by perimeter monitoring or geofencing, giving them the tools to confirm threats, identify alerts, prevent false alarms and provide essential context during emergencies. All from a single device. Add on the full suite of wireless integratable devices like panic buttons and door, motion, glass break and water leak sensors, and these alarms offer one of the most comprehensive and proactive security systems available on the market. This is especially true when compared to a traditional “bells-only” alarm, which only raises an alert after the building has already been breached.

On Demand Alarm Control
When your alarm is activated by a door sensor or motion detector, you’ll get a push alert to your mobile phone, showing exactly when and where it was triggered. You can even sync a camera to the app to show direct video footage of the event.
Remember:
- Real-Time Alerts
- CCTV Visual Verification
- Fewer False Alarms
Features of Cloud Access Control
Cloud based alarm systems offer complete visibility over your business premises, with dynamic colour-coded dashboards showing the status of the alarm, whether in one location or multiple. This feature is ideal for travelling business owners who entrust staff to lock up the premises each evening, as it allows the operator to actively check their alarms are set from any worldwide location with an internet connection.
The alarm interface can also be used to monitor fire escapes and delivery bays during working hours, sending real-time alerts and notifications if they’re left open or compromised.
Using the control interface on a smartphone or other internet-connected device, property managers will gain full-view access to their alarms, enabling them to deactivate and reactivate as they need.
This feature is particularly useful for instances with out-of-hours cleaners, late-night deliveries or staff working late, as the operator can arm/disarm as approved visitors come and go - preventing unnecessary alarm activations without needing to be physically on-site. Paired with a cloud-based access control system, users can monitor the occupancy of the building and re-set the alarm once there is no one left inside.
Powered with AI threat detection, custom alarm conditions and video verification, cloud based alarms dramatically reduce the chance of false alarms on your premises. If a suspicious breach is detected, the alarm will alert the Site Admin, and connect them to the integrated camera to verify the threat. This limits the chance of wind or wildlife causing a false-positive, reducing the risk of wasting police time or needlessly disturbing surrounding neighbours.
With custom alarm conditions, admins can also set and define specific triggers for each alarm area. All received CCTV images are analysed by proprietary machine learning algorithms. An alarm is only activated when the artificial intelligence determines that the trigger is an actual intruder or threat, as per the set alarm conditions.
High quality cloud alarms come with highly secure, password-gated user interfaces. These can only be controlled by pre-authorised individuals, making it near impossible for fob misplacement, theft or cloning.
In the cloud interface, operators will be able to easily assign specific alarm permissions to their workforce - from Site and Live-Only viewers to No Access users. Rather than assigning each necessary user a keycard or control fob, operators can grant remote or mobile control over their alarms to their trusted site managers, and edit these permissions as and when they need.
By integrating a cloud based alarm with outdoor CCTV cameras, users can set up virtual zones and video tripwires to trigger when a boundary is crossed. Using a motion search interface, users can mark specific areas of interest for each CCTV camera on their premises, adding filters to trigger an alert when people are in the scene or within a certain time window. With facial recognition, this can also be set-up to trigger for specific persons of interest, like known shoplifters, repeat offenders or former employees.
Using onboard analytics, the connected cloud cameras will record high resolution video when movement is detected, sending an image to the cloud for AI verification, ensuring users are only notified for actionable events rather than lighting changes or weather-related movement. If a human is detected in the frame, a rapid notification will be sent to the operator to view footage and take immediate action.
Responding to an alarm activation can be unsettling, stressful and frustrating - especially if it's a false alarm. With a cloud alarm system, your maintenance provider or Alarm Receiving Centre (ARC) will be able to deactivate a false triggering alarm and resolve the issues entirely remotely, saving you the expenditure of a technician call-out.
Smart Alarms: Everything you Need to Know
If you’re concerned about the security of your burglar alarm, it may be time to consider a smart upgrade to protect your home. But what is a smart alarm? What can it do for you? How does it differ from a normal “bells-only” alarm?
.png)
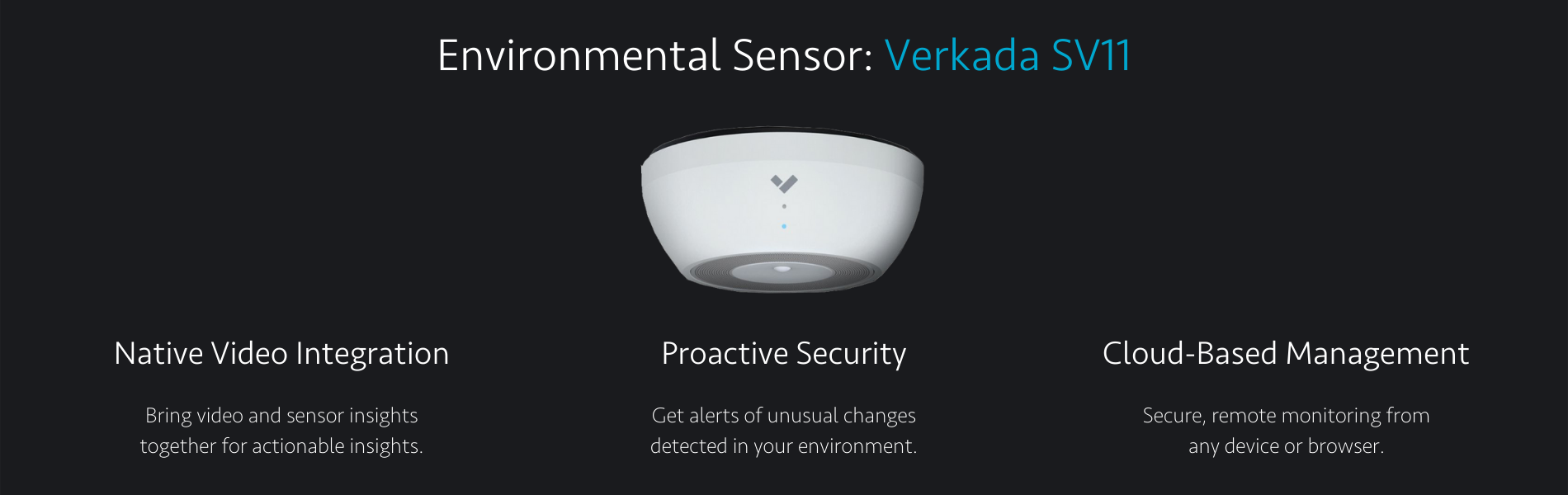
What Are Cloud Sensors?
Cloud sensors are powerful all-in-one units designed to monitor environmental, air-based or sensory changes in physical spaces. Loaded with a collection of high-spec sensors, these devices measure air quality, humidity, temperature, motion and noise.
Sensors can be accessed and managed through a web-based command platform in the same way as other cloud security devices, like CCTV or access control. They provide context for any environmental changes instantly. Operators can set custom alerts and quickly scan real-time data to see where people are and what’s happening at each location on a reactive meter-style reading.
These systems make a sensible addition to any serious security operation. Natively integrated with cloud based alarm systems, activity like motion and noise can be set up to trigger an alarm in off-limits zones, or sensitive areas where video surveillance is non-permitted, like bathrooms and changing rooms.
In video-permitted zones, sensors can be integrated with CCTV cameras to give video playback of sensor-based events. A sensor reading, such as a smoke alert, can trigger an alert on the operator's phone, prompting them to visually confirm the issue on a nearby connected camera.
From an environmental perspective, sensors can offer valuable temperature and air quality insights for server rooms or controlled manufacturing facilities, helping site managers to keep safety a priority. These systems can also detect vaping and smoking events, allowing site managers or even school managers to keep a watchful eye over their occupants in hard-to-reach corners. Discover: What Are Cloud Environmental Sensors & How Do They Work?
Highly accurate temperature measurements have a number of advantages for businesses, from a safety and operational stance. Verkada’s SV11 sensor is accurate from -5°C to 50°C, giving operators custom temperature alerts for each specific sensor.

Monitor the relative humidity in each room. Detect changes in the amount of moisture in the air compared to the temperature and receive instant notifications for chemically-induced humidity changes that could threaten perishable stock or employee health.

Receive instant, automatic alerts for chemicals evaporating into the air including benzene, ethylene glycol and formaldehyde. TVOC is “Total measure of Volatile Organic Compounds”, the chemicals mentioned previously, which can be extremely damaging to human health and wellbeing.
Monitor the total noise level in each area. Under GDPR law, private conversation cannot be recorded, so audio will not be saved by the sensor. However, a decibel reading will be available in the interface or as an instant notification above a certain level. Operators will be alerted to sudden jolts in decibel reading, allowing them to respond to accidents or emergencies quickly.

Particulate Matter 2.5 (PM 2.5) refers to tiny inhalable particles or airborne droplets that can have a dangerous effect on human health. These are usually caused by dust, vehicle exhaust, burning fuels, cooking, smoking and vaping in enclosed spaces.
Unique to Verkada sensors, the Vape Index is a score derived from multiple sensors that detect compounds closely linked to vaping or smoking. Vape Index measurements outside of the “green zone” suggest suspected smoking activity, but could also indicate dangerous fumes from other sources like gas fires or fuel burning.
Motion sensors are particularly useful in detecting suspicious activity in off-limit zones or out-of-hours. Measuring the changes in infrared light absorption, the sensor can raise an immediate alert for any movement on-site.

Keep student health and safety a priority in recording-sensitive areas. By installing an environmental sensor, you can safely monitor bathrooms and changing rooms for vaping, bullying and fighting, without fear of breaking relevant GDPR or privacy regulation.
Room temperature can be unpredictable. With ingrained humidity sensors, you can track changes in the air's moisture quickly and effectively. This helps you to act quickly when your expensive servers, data and electronics are at risk of moisture damage.
Protect valuable texts, paintings and artefacts from moisture damage, temperature changes or evaporation. Environmental sensors are ideal for environments that demand consistent air quality control like museums and archive rooms.
With a connected environmental sensor, you can ensure stock is kept at the optimal humidity around the clock. Reduce loss or deterioration of climate-sensitive products, ingredients and records caused by shifts in humidity.
Track occupancy and space utilisation in your buildings without needing to install expensive surveillance equipment - or break any privacy laws. Sensors can also raise alerts for excessive noise in apartments or office spaces to support claims or complaints.
.png)
Hacking & Cybersecurity
The ability to access security systems over the internet naturally raises concerns for end-users over hacking and cybersecurity threats. Cybercrime is continuing to grow at an alarming rate. 400,000 incidents of fraud and cybercrime were reported in 2021 alone.
Cloud security companies are aware of this flaw, meaning it is rarely an afterthought - or a last minute consideration. Devices and SaaS packages are generally designed to be ultra-secure from the very first step, starting with the hardware design, to the interfaces that store the data.
Automatic bug patches, fixes and firmware updates are part of any good cloud security set-up. These ensure that the systems are constantly up-to-date with the latest regulations, without any breach points or backdoors. These regular updates mean the chances of cameras, alarms, access controllers or even security apps being hacked are actually very low. There’s an endless number of access control and CCTV systems in use today that haven’t seen a single Windows update since installation.
Despite a number of high-profile cybersecurity breaches in the cloud security industry in recent years, the reality is that these instances have largely been down to human error. Weak passwords. Credential misplacement. Over-sharing. These all play a factor in the security of any system - whether cloud based or otherwise. By remembering the basics of digital security, users will undoubtedly keep their cloud security system ultra-secure and hacker-proof.
With automatic firmware updates, cloud security devices are continually upgrading and improving alongside industry innovation. Put simply, the day you have a cloud-based security system installed, that will be the worst version of that system you'll ever own. It will only ever improve with the latest features and algorithms, making the solution even more secure as time passes.
Similarly, if a new wave of cybersecurity threats emerges, providers like Verkada are able to automate patches to combat these in rapid time, preventing hackers from remotely accessing cameras, data storage or other devices illegally.
Providers like Verkada and Avigilon Alta are trusted cloud security manufacturers with a security-by-design approach. Reputable, well-known providers have the infrastructure behind them to penetration test their systems, with developers continually working to further their security. Certain manufacturers will even have their systems audited or “hacked” by third-party developers to test the effectiveness and reliability of their products.
Strong cloud based security should feature encryption on all data in transit over the network. Encryption adds an extra layer of security to all data operations, preventing malicious interception or eavesdropping.
All cloud based control interfaces are powered with foolproof audit trailing to detect activity changes, both as they happen and reactively. Using proprietary algorithms, users can observe physical and digital sabotage from a number of sources, both for internal ones and external data breaches. Essentially, for businesses with multiple admins, operators can monitor all changes made in the archive, adding an extra layer of security to their operations.
While cloud security systems do rely on internet connection for full functionality, hardware offered by brands like Verkada and Avigilon Alta will continue to perform, even if the network connection drops.
Without a connection, users will lose out on phone notifications and alerts, but cameras, alarms, sensors and detectors with a connected power source will still record or trigger if a breach is detected, reducing security downtime and making them no less secure than a standard legacy system.
.png)
Cloud Security: Key Considerations
Switching to the cloud can seem like a daunting change, but we would urge you to explore how cloud technology could benefit your security operations. In most instances, the advantages are simply unmatched.
Of course, cloud isn’t for everyone. While there are many huge benefits to its use, an on-premise system can still serve a purpose, such as residential settings storing minimal data or in highly secure government buildings with hard drives guarded by manned security.
As a business owner, it’s your duty to protect your employees, customers and their data under GDPR law. If you’re looking for a system that can do this efficiently while also helping to boost your business operations, cloud security is likely the right fit. There are a few key points to consider before making the switch:
1. Look for Verified, Quality Manufacturers
2. Don't Be Constrained by Legacy Systems
Switching to the cloud doesn’t need to be an immediate transition. Smaller businesses have reaped the rewards of scaling their security systems gradually, rather than ripping and replacing all in one go.
There are cloud based products on the market that can sit alongside your existing legacy systems without compromising on security or quality. We call this a hybrid cloud system, and it's a perfectly viable security option. For example, you can buy a cloud connector to store your video data digitally from traditional IP-based or even analogue CCTV cameras. These provide on-premise and cloud functionality, allowing you to make that first step towards a full, cloud-managed system.
3. Take Small Steps
Cloud migration doesn’t have to be an all-or-nothing approach. You don’t have to move your entire system over to the cloud from the get-go. It’s possible to move slowly and break it into budget-friendly chunks.
By working with a trusted provider, you’ll be able to scale your security system over time. A good security provider will help you grow your security network with new devices that complement the existing ones in place. This allows you to keep your business moving forward and re-invest capital into your security at the most suitable times.
Thanks to SaaS packages offered by companies like Verkada, you can even pay for your security on a monthly, rolling subscription basis, saving you from the expense of an upfront, one-time fee.
4. Work with the Right Installer
A robust, enterprise level Cloud security system is complex to install and specify. Business owners and site managers who attempt to install or specify/design these systems should be concerned that they won't get the most out of the very expensive system they have purchased. Involving a professional will provide you with real-world working experience as to what works and what doesn’t.
If you’re looking to get in the cloud, you need to work with a trusted, reliable and knowledgeable installer. A professional provider will be able to ensure your technology is running at peak performance and connected with all the other devices in your network, saving you from risking security downtime, or from missing a potentially fatal backdoor in your security.
Professional installers can also support your business from an operational standpoint. Using their expertise, they’ll be able to set up video analytics, AI integration and custom settings that help your employees work smarter, rather than harder. From stock counting, queue monitoring, occupancy management or even site HI-VIZ detection, the right provider will be able to show you the full potential of this technology.
The design of these systems, including camera placement, resolution and environmental capability, take years of skill and experience to get right. A professional installer will work with you to define the objectives of your system, and design a setup to meet those aims.

Final Thoughts
Looking to upgrade to cloud security? If you’re concerned about the reliability and sureness of your technology, now is the time to upgrade. Ignoring the attractive benefits cloud security has to offer your home or business could cause troublesome (and expensive!) issues.
Have any more questions about cloud-based security systems? Check out our blog!
At Chris Lewis Group, we understand the importance, reassurance and convenience cloud security can offer your building and occupants. Our installation experts are highly experienced in the specification, design, installation and aftercare of cloud security solutions.
Working with industry leading technology, we design bespoke security solutions that are unique to your building and needs.

.png)
.png)
.png)



.png)
.png)