Access Control: An Introduction
Access control systems can be seen in all facets of our lives; from the fingerprint scanner and facial recognition on your phone, to the PIN pad you use to enter the gym or the key card you use to get into the office.
There are very few businesses today that don’t benefit from access control in some form. For this reason, the global access control market itself reached a record valuation of around $15.3 billion in 2021.
In this guide, we’ll cover everything you need to know about physical access control, and how it can play a role in the security and operational smoothness of your business.


What Is Physical Access Control?
Physical access control refers to a form of electronic security system that is designed to control who has access to specific areas at any given time. At their most basic level, access control systems are designed to restrict access to only authorised individuals, providing a way to control who enters and leaves the building.
When we refer to access control, we’re typically talking about an electronic security system. These solutions usually include a reader and a "credential" or identifier - generally in the form of a key card or fob. More recently, types of credential have grown to include mobile phones, fingerprints and faces. Not only does access control provide security for your building by restricting access to certain people at certain times, but all of these solutions can log who accessed where and at what time. This means they can provide businesses with insightful data to support HR operations or help them understand how (and when) the building is being used.
There’s no one-size-fits-all definition for access control; it’s a broad term that can include guards, electrified doors, turnstiles, fences, gates and many other security measures. It tends to be called ‘physical’ access control to differentiate from "virtual" access control, that prevents people from accessing computer networks in the IT world.
Throughout this article, we will explore the applications, benefits and use-cases of physical access control, including: types of hardware, credentials, key components and other installation considerations.

How Does Access Control Work?
In an access controlled building, authorised people use their credentials to make unlock requests at readers, which send information to an Access Control Unit (ACU), also known as an access control panel or a controller. The ACU will query the database of authorised credentials, reference the time and release the door by triggering an electric lock to release. We break down how access control works into five steps:
1. Authenticate
A user is authenticated when they present their credential to a reader. The credential’s data is sent to the Access Control Unit (ACU), where it is analysed to determine whether the user is known and recognised.
2. Authorise
Next, the access controller determines if the user is authorised to access this particular area. Are they using the right kind of credential for this door? Are they attempting to unlock the entry outside of specific door schedules?
With a solid access control system, to be granted access a user must:
-
Have access to the entry they’re trying to unlock
-
Use one of the predefined credential types
-
Make the unlock request within any predefined door unlock schedules.
3. Access
Once the user is authorised, the Access Control Unit sends a command to the door locking hardware to unlock. In the instance of electromagnetic locks, power is temporarily interrupted when unlocked (also known as a fail-safe), whereas with door strikes, power is temporarily applied to unlock the door (also known as a fail-secure).
4. Manage
Managing an access control system includes adding or removing entries, users, credentials, schedules, and alerts using administrative software synced automatically with Internet-connected or networked ACUs. The newer cloud-based access control systems integrate with directory services like Google G Suite and Azure Active Directory. This means users no longer have to be manually added to or removed from the network, this process is automated as they are instead added to or removed from these integrated tools and workspaces.
5. Audit
Administrators can audit access control systems by generating reports for access logs, including both user activity and entry activity. This is useful for general system reviews; ensuring that the system is working as expected and that there are no issues with accessing entries. Reports are also helpful for meeting compliance standards, such as HIPAA, that require a certain level of physical access control. Additional audit capabilities are provided by access control systems that integrate with Visitor Management Systems, Video Management Systems (VMS), and other security-type platforms.

Types of Access Control
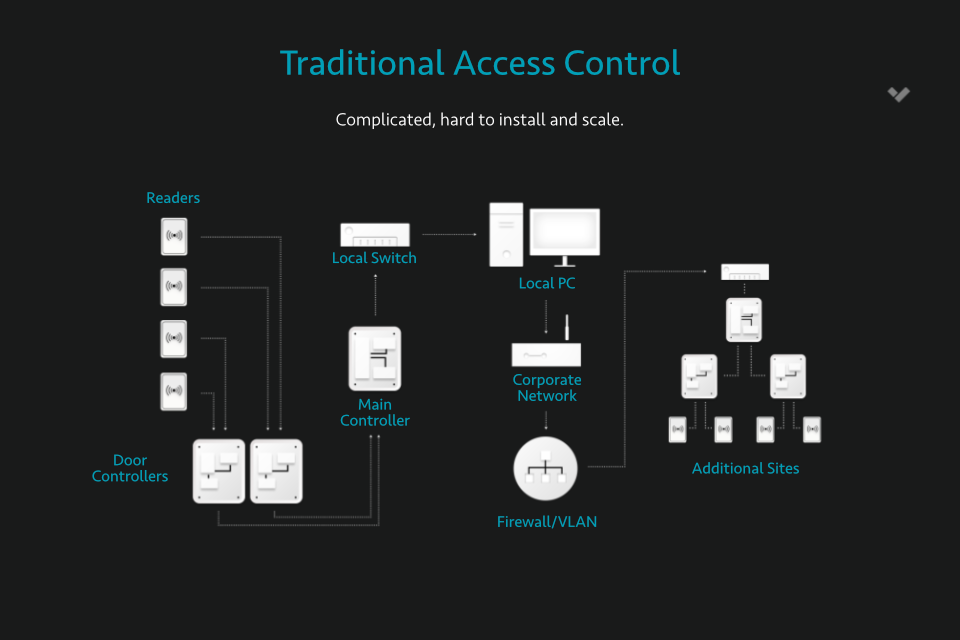
There’s no one-size-fits-all when it comes to business security technology. While a good installer will be able to advise you on the best system for your specification and brief, it’s always worth taking the time to research the most appropriate system type for your needs. Physical access control systems are broken down into two basic types: Standalone and Network.
Standalone is the simpler of the two main categories. In this system, each access point on the property is isolated from the rest. This means users need to be added to each access point individually and manually.
This is great for a smaller location with few users that is looking to install its first access control without too much expense. However, for a larger location, especially one with a large workforce and higher employee turnover, ensuring only employees are allowed entry would be a nightmare, as it would need the system administrator to roam the building, adding and removing users from access points one-by-one.
A network access control system is the more complicated of the two, and refers to a solution where all access points are linked to a central control software. Users can be added and removed across multiple doors without having to walk the building. You can also restrict access at certain times of day and generate activity reports and audit trails. There are two subcategories of Network Access Control System: "On-Premise" and "Cloud-Based".
In On-Premise systems, the server managing the network of controlled access points is located on-site. This means all access points will be administered from one or more PCs and users can be added to or removed from all access points at once. This is either done by changing individual user permissions, or by assigning users to roles that have set permissions. Typically an on-premise system is not connected to the internet, providing an extra level of security, as this means the access control system cannot be accessed remotely by hackers from outside the building.
Cloud-Based systems are similar to On-Premise systems, in that the access points are all linked to a central server. However, instead of the server being on-site, it's remote, connected via the internet. This means that the server can be viewed through apps on tablets, PCs or mobiles from anywhere in the world, as long as the correct login is used. As with On-Premise Access Control Systems, users can either be assigned permissions individually or their permissions can be based on their job role, and this can all be done remotely, rather than at each individual access point.

Types of Access Credential
In access controlled buildings, authorised people use a specific “identifier” at readers to make unlock requests and gain access. These “identifiers” are known in the industry as credentials - and there’s a wide variety of different types available. Access control has come a long way since the days of keypads and fobs. Today, businesses across the world are being accessed with a wide range of credentials - from mobile phones to fingerprints and facial recognition.
You can also combine two or more identification methods to improve the security of your building. This is called verification and it’s a common practice in buildings housing expensive goods or data. For example, in a bank, you could require visitors to use an access card for identification and then ask them for a fingerprint scan for full verification.
Credentials typically come in three different categories:
Something you have: Such as a key card or key fob
Something you know: Such as a PIN or password
Something you are: Biometric identifiers
These come in two main forms, key cards and key fobs. They can also work in two different manners, actively or passively:
Passive Proximity: Relatively cheap cards or tags with small chips inside. They transmit the user number to a reader from a short distance (>15cm) away. These are harder to clone and typically have a longer lifespan as they receive less wear.
Active Proximity: These cards use batteries to offer a longer range than their passive alternatives. Active cards and tags are usually used for long-range access readers, like those needed for vehicle access or for “hands-free” access. Typical reading ranges vary from 0.5m to 10m.
Keycards: Keycards are still the most common credential used in access control systems. While these will offer an affordable and easy-to-use option, keycards can be lost, or stolen and cloned, potentially leaving you vulnerable to card-cloning.
Fobs: Like keycards, fobs are an extremely popular credential for businesses across the globe. These typically take the form of a scannable, plastic RFID token. However, for major employers, creating fobs for each individual user will come with an expensive up-front cost.

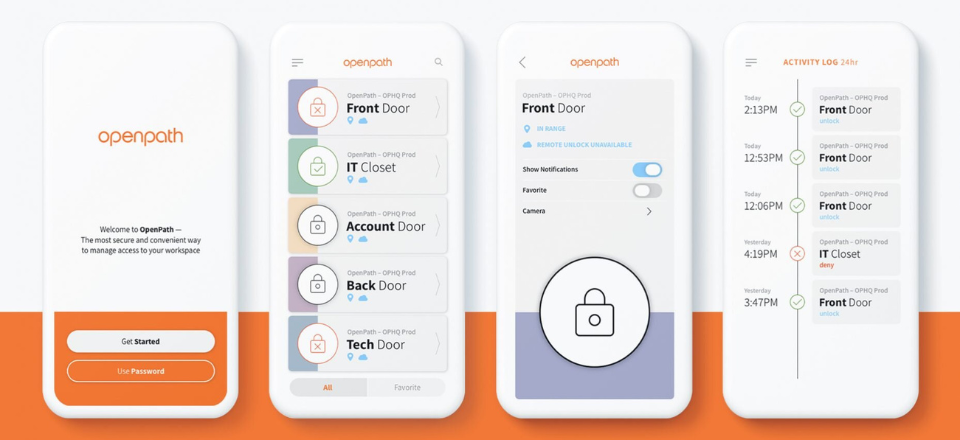
Mobile credentials are controlled via a secure smartphone app on registered devices. Thanks to passwords, Face-ID and fingerprint control on most smartphones, modern mobile credentials are essentially dual-factor authentication. To access the building illegally, not only would you need someone’s phone, you’d also need their unlock code or biometrics to get to the access credentials. You can use a slightly lower security setting on the phone too for convenience, which enables the door to detect a nearby phone and release without having to unlock the phone.
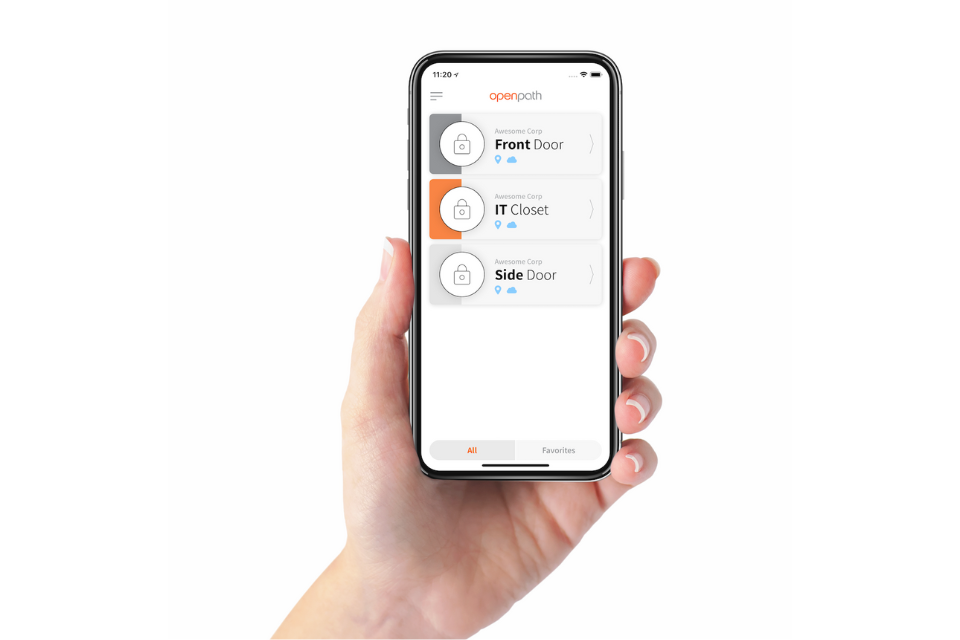
Used in schools and businesses for decades, PIN readers rely on a specific code rather than a physical credential. Depending on the model, a PIN reader may operate as a standalone code for each room, or can be tied to an access control system to issue unique codes for each person. For obvious reasons, this is the lowest form of security as PIN codes can be shared. If you do opt for this approach, we would always recommend changing PIN codes regularly.

Biometric access draws on human data to permit entry, including fingerprints, iris scanning, facial profile and voice patterns. Biometric data gives you the certainty that the movements around your premises and within are true to what your system has reported. It removes the room for human error and deception, by using aspects of our genetic makeup as a means of access, as the elements of this are beyond the control of others - or even ourselves.


Other Key Components
Aside from credentials, there are a few other core components that are included in an access control system. While this is generally taken on a system-by-system basis, most modern access control solutions will feature locking technology, readers and software that assists organisations in collating, storing and processing their access data.
Scanner-like devices that are installed near access points within the building. They’re used as the main touchpoint for user credentials, with users typically touching their credentials on the dedicated pad to send a permission request to the control panel.

The entries to your property like doors, gates, turnstiles and elevators. Door contact sensors indicate whether a door is open or closed, propped or forced open. Request to Exit (REX) sensors and buttons are used to unlock doors automatically when someone exits via an access point.

Traditional door access points are usually configured with electric strikes or electromagnetic locks to bolster the sturdiness of the system. These additions reinforce the strength of an entry point, making it far less vulnerable to lockpicking or brute force attacks. You could have the most secure form of credentials and access control system, but if you have the wrong lock, it could be pointless. Careful consideration should be made when selecting an electric lock for your doors. We recommend that you consult a professional company for specification and installation.

These control panels receive credential data from dedicated door readers, which decide whether a user has the correct access permissions. The control panel, or ‘controller’, manages the entry process, instructing the access point to permit or deny access. These should always be installed on the secure side of the access control door, otherwise these devices are at risk of being tampered with.

PSUs are the energy sources that drive the electrified access control hardware. A suitable PSU should be used for each controlled access point in the system, in line with the manufacturer's recommendations. In the event of a mains failure, systems should be powered with a battery backup.
.png)
The access control hardware communicates to an on-premise or cloud server which hosts a database to authenticate users. This application defines users, credentials and access schedules. The software helps users to report on space utilisation, access peaks and occupancy.

Access Control Storage Options
Like other security solutions, most commercial access control systems fall into one of two categories: cloud-based and on-premise. This is a key decision for architects and business owners alike during the system planning phase - and there are positives and drawbacks to both systems.
On-Premise Systems
On-premise systems rely on a dedicated local server, usually kept on-site. This technology requires a connected computer server running the necessary software and connected to the hardware on-site, including controllers, sub-controllers, readers, power supplies and electrified door hardware.
On-site servers need maintenance and updates, occasionally go wrong, can be physically damaged and require complicated VPNs to access the software remotely and in a secure manner.
Although you will lose the remote accessibility, having your system completely disconnected from the internet will prevent the system being hacked from outside the building (though this type of cyberattack is rare, and vanishingly unlikely for a smaller business).
For some businesses, local data storage makes sense. On-premise systems enable businesses to take control of their own data storage and security, without the interference of a third-party. Naturally, this means that less data leaves the company’s hands, providing greater assurance in specific cases.
Unlike cloud-based systems, on-premise access control remains on location and without an internet connection for access. This means that data is always accessible, without risk of disconnection or interruptions.
On-premise systems are very limited in terms of scalability. If you’re looking to set up a traditional on-premise access control system connected to multiple other sites you will need to set up VPNs to connect the various sites together. Plus, each additional location will require a new installation, dedicated manager and new licence. Should you wish to expand your system beyond the resources of your server, you would need to upgrade or replace the technology.
Similarly, most legacy systems are limited in terms of credential type and third-party integrations, making them more susceptible to ageing and expensive upgrades.
Each server must be updated manually each time a new windows or software update is released, adding additional pressure to IT teams and putting the security of the business at risk each time a patch or firmware update is ignored.
An on-premise system is limited to the storage capabilities of the connected hardware servers. The business will have the responsibility of regularly updating and clearing out old data and credentials to ensure there is enough space for the system to operate effectively.
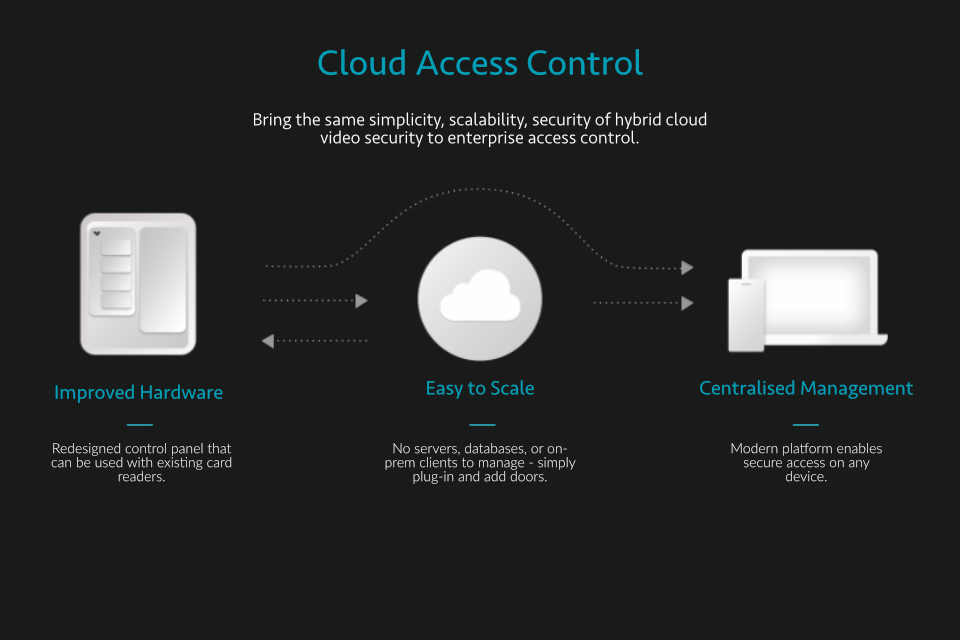
Cloud-Based Systems
Cloud-Based access control systems run software and storage in the cloud via a remote server that frequently syncs with the local ACUs - without any dedicated storage held on-site. As the server is cloud-based, it’s easily connectable from any internet-enabled device. This gives operators the ability to add, remove and update permission on-the-go from anywhere with web access.
Cloud also enables businesses to easily connect third-party authentication systems for single sign-on such as Office 365 or Okta, making it possible to automate access permissions inside your business as people come and go. Essentially, the cloud makes managing door control one step easier and more accessible for the operator - but more secure at the same time. As the system is hosted in the cloud you have a much higher uptime and you will never lose data due to physical component failure of an on-premise server.
With cloud control, operators can send a user credential to an employee's phone, have them download an app and register for immediate access through Bluetooth, Wi-Fi, 4G or the phone’s built-in NFC chip, making it near impossible to duplicate, clone or forget.
Using plug-and-play ‘Access Controllers’, users are able to instantly connect new and existing door readers on multiple sites to their cloud system through an Internet connection, without needing to configure new VPNs, firewalls or additional servers across multiple sites.
With automatic firmware updates, cloud security devices are continually upgrading and improving alongside industry innovation. Similarly, if a new wave of cybersecurity threats emerges, providers like Verkada are able to automate patches to combat these in rapid times.
With remote monitoring and live access reports, cloud access control systems enable operators to respond to entry threats, tailgating or security breaches as they happen. If an unregistered user attempts to gain access to the property, or if a door is being propped open, a signal will be raised to the operator. Users can also access the historical timeline and audit trails of the events from any connected device.
With full remote maintenance and automatic firmware updates, businesses can essentially keep on top of the latest security innovations without risk of falling behind. This makes it easier to respond to emerging threats and saves money on hardware upgrades and maintenance callouts.

Installing Access Control
An assured enterprise-level access control system can be extremely complex to configure, install and specify. Business owners or site managers looking to implement access control should always proceed with caution - and take the time to research and fully invest in their technology before purchase or installation. There's a lot that can go wrong.
With hundreds of solutions on the market, determining the right fit for your business will ultimately depend on a variety of factors, including budget, industry, risk and time. Whether you’re working with an installer, architect, a project manager or simply researching on your own, there are five crucial steps to take in the installation process.
1. Assess your Requirements
There’s no one-size-fits-all approach to access control. Every business, building and educational establishment will face its own unique security challenges and businesses often pay the price for choosing a system that doesn’t match their requirements. The first thing you need to do is assess your current situation, and understand what you want to achieve.
- How many doors are you looking to secure?
- Do you want a PC-based system to be able to download audit trails and add and remove users from a central location, rather than walking the building to amend codes or delete fobs?
- Do you want to know how many people are in the building for Roll Call?
- What are you trying to protect?
- Do you want to integrate with other systems?
- Have you considered using mobile phones for access control credentials?
- Do you want to integrate visitor management into your system to allow visitors to navigate the building more easily?
- Would you like the convenience and added security of using your fingerprint or your face as your access control credential?
- Do you want credentials that can’t be copied?
- Do you want to report on space utilisation?
2. Consider Integrations
Access control should be considered as an addition to your security network - not the be all and end all. With that in mind, businesses should always look for technology that is compatible with their existing systems to build an integrated network of tech that work together to keep the building secure.
Most buildings have some type of video surveillance in place to ensure employee safety and bolster the business against theft and other petty crimes. Today, these CCTV cameras can be integrated with access control systems to perform more complex functions such as video verification, people counting, automatic number plate recognition (ANPR) and more.
3. Look for a Trusted Installer
It’s never worth compromising the quality of your technology with an inexperienced tradesman or DIY job. Get it right the first time by investing that time and effort into finding a reliable access control installer. Look for the NSI Gold Accreditation on the provider's website - this will mean they can install and service your system in line with industry standards.
A good professional will take care of the entire process from start to finish. Access control experts like Chris Lewis Fire and Security will be able to scope out the ideal solution for your business, helping you to understand everything from integration to setting up credentials.
4. Set Up Credentials
Once your system has been professionally installed, you can begin to set up user credentials for each of your employees and occupants. Usually, this is a simple process, as using a user-friendly app or software means that users can add, edit and assign credentials without needing a thorough understanding.
A good installer will support you in this process, making it easier for you to train other administrators in your business. If you’re looking for a quick and efficient way to issue new access tokens, mobile credentials are a strong choice. It’s quite literally a case of sending a user credential to their device, having them download an app and registering for immediate user access.
5. Find a Maintenance Provider
With a range of moving parts and hundreds of users passing through on a daily basis, regular maintenance is the only way to ensure your new access control technology is meeting its full potential and keeping your staff protected.
Installation is only one side of the coin. By taking the time to invest in a reliable maintenance provider, you’ll be able to keep your system running smoothly and at full speed, responding to common faults and preventing new ones. Not to mention, this technology is always improving alongside industry innovation. A good provider will identify where you are at your weakest, helping you find the right time (and place!) to upgrade.

Security Levels: Understanding Your Requirements
Under British Security Industry Association guidelines, access control points are graded according to the type of business and risk associated with the premises’ security. The grade applies to the protected area and not the overall system, meaning mixed grades can be applied within any premises. You may have four Grade 1 access points in some areas, and Grade 4 in others - it all depends on the nature of your building.
The grade applied to your access points will provide a good indication of the level of security needed, and the recommended technology for each in your building. This helps business owners, installers and architects meet their requirements effectively and within budget.
A standalone lock (code, PIN or token), or offline system that is controlled in a public area for low-risk situations.
This grade is typically applied to internal doors or areas where public needs to be limited, such as University classrooms or staff rooms at a library.
An online system utilising tokens or PINs to prevent access to the premises. Events are received in real-time on the monitoring software.
This grade is typically applied to commercial offices, small businesses and hotels. Classic keycards and fobs should be avoided for these premises due to the increased risk of cloning and duplication.
An online system using two-factor authentication or single-factor biometric to prevent access to the premises. Events are received in real-time and tracked on the monitoring software.
Grade 3 is typically applied to secure areas of commercial business such as server rooms, data centres or stock rooms housing expensive products.
An online system using two (or more) factor authentication, one of which should be biometric or human image verification to prevent access to the premises. Events are received in real-time on the monitoring software.
Typical applications of Grade 4 include high security areas, such as government buildings, data centres or private facilities that are vulnerable to theft or crime.

Applications, Benefits and Opportunities
There are multiple benefits to installing access control. Aside from the clear security perks, modern access control can help businesses intelligently take care of their HR operations, monitor occupancy and control off-limit zones. In addition, integrations with other Internet of Things (IoT) technologies can provide additional benefits, in terms of security, comfort and operational efficiency.
Anti-passback can be used to stop occupants from passing their credential over to another person outside the area after gaining entry. Anti-passback rules can be reset after a preset period after valid entry, at a fixed time each day, on exit from site or manually as an override.

Anti-tailgate is a feature designed to prevent physical security breaches where an unauthorised person follows a valid user through a door at the same time or immediately after. This technology can deter this action through notification or restricted movement (turnstiles etc).
Hard Anti-Tailgate: Employs physical means of prevention such as turnstiles to restrict movement.
Soft Anti-Tailgate: Raises a red flag such as a system alert or triggered alarm if unusual entrance activity is detected.

Lift control is a beneficial addition to multi-story corporate buildings and facilities. Using an individual’s credentials, staff members can be granted access to floors, rather than solely doors. For instance, a reader can be fitted in each lift cab, using technologies compatible with the rest of the system.

Linked to a dedicated CCTV camera, access control can be automated to enable access in and out of car parks through the use of ANPR. A camera is used to capture the image of the vehicle’s number plate, which is compared against a list of authorised vehicles stored in the database.
Cameras should be installed where vehicles are lane-controlled or constrained by narrow widths to improve the accuracy of the technology and prevent tailgating. It is also worth including measures to restrict this risk, such as speed humps, barriers or electric gates.

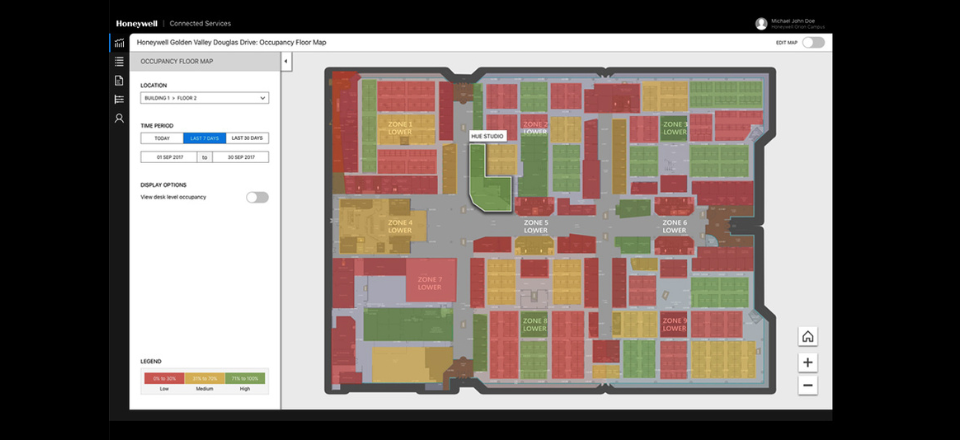
With access event timelines being stored digitally, cloud access control presents a unique opportunity for businesses to actively monitor their occupancy and capacity. From an HR perspective, businesses can keep an eye on staff arrival times and occupancy percentages, to identify unreported absences that may have slipped under the radar.
Occupancy monitoring can also be used to proactively monitor capacity in specific zones of your building that require management, such as car parks, staff cafeterias or gyms. Readers can even be remotely programmed to automatically deny new entries until capacity falls below a preset number.
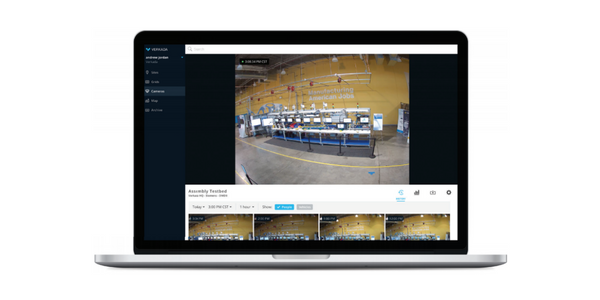
Cloud-based access control can be taken the extra mile with CCTV integration, giving users 24/7 visual access to their controlled doors. With the right setup, users can arm their access control with facial recognition and visual confirmation of every user that passes through the entrance, backing up the audit trailing with video evidence.
Cameras can also be used to proactively detect user tailgating or doors being held open. By intelligently recognising these events using video analytics, the system will alert the admin on their mobile device, allowing them to respond to access alerts safely and proactively.

A modern access control software solution can support businesses in all areas of their operations, with access alerts, exportable heatmaps, entry event timelines and occupancy monitoring an ingrained part of most modern cloud solutions.
Access control software can support HR operators in better understanding abnormal events and patterns on their premises, such as absenteeism on particular dates or continual lateness. For example, if an employee is repeatedly off sick or late on the same day every month, the system will notice this, providing quick insights to help you make more informed decisions.
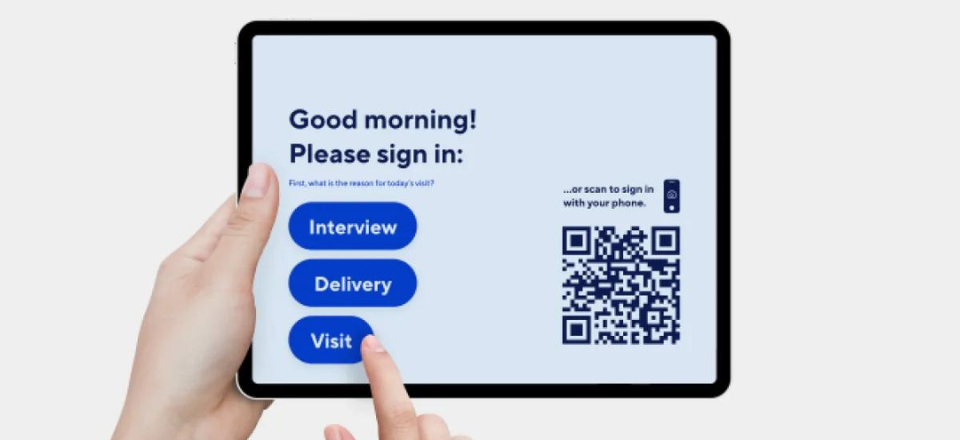
With visitor management integrations, organisations can operate more efficiently as processes are automated. This means that reception staff have to spend less of their time processing access requests, and visitors spend less time signing in. With some solutions, expected visitors such as contractors can be issued with one-time credentials remotely so they can just turn up and gain access to where they need to go for the day. Alternatively, unexpected arrivals can be screened more effectively with touch sign-in or a connected screen or tablet.
.png)
Physical Access Control: Key Considerations
For a newcomer to access control, it’s easy to get lost in the details. From specifications to system design, access control installation is a multifaceted process that takes time to get right. When ready to proceed with your installation, be sure to ask yourself the following questions to ensure your chosen system is right for your business:
While some manufacturers allow anyone to purchase and install their hardware, it’s never worth trusting anyone but a professional with the security of your business. A good installer will be able to help you in your system selection, as well as handling the specific elements of your building.
If you’re upgrading from a legacy system, it’s always worth looking at an access control solution that is backwards compatible with the existing hardware. This will make the process of wiring and setup faster and smoother, meaning access control installers can deploy hybrid systems without compromising on efficiency, convenience or budget for the client.
The initial installation is only part of an access control system plan. Facility owners and site administrators will also need to consider the maintenance processes required to keep their systems running.
Electronic access control systems are dependent on a variety of different technologies, from Wi-Fi to RFID, NFC and biometrics to name but a few. Under all circumstances, access control requires 24/7 uptime for full effectiveness. However, issues such as misread fingerprints, electrical shortages or internet outages can cause a system to fail.
If you’re a facility that requires constant uptime, it’s worth looking for a system that can facilitate that, and investing in superior-quality hardware to ensure it is stable. Businesses that invest in cheaper technology tend to pay the price with worsened uptime, unresponsive credentials and even cybersecurity breaches.
Integration doesn’t need to be overly complex - but it is a necessity for a fully-fledged commercial security network. If you want an ultra-secure access control system, it’s always worth looking into the integration opportunities between the system and your other devices.
This could be a simple integration between card-activated door handles and a cloud management solution, or more advanced integration involving intelligent fire alarms that can open all entrances in the event of an emergency.
Ease-of-use should be a priority for business owners installing access control for the first time. The right system should enable employees to enter and exit the building without any added hassle. It should also help specific teams like HR to work more efficiently using the dedicated dashboards, exportable heat maps and people-counting functionalities. For businesses with a large number of employees, it’s a good plan to opt for cardless technology such as mobile credentials to avoid queuing or delays.
The modern workplace is constantly evolving. Now, more than ever, companies need to adapt to support flexible workers. In addition, they also require solutions that can integrate with the various apps they already use at work. Businesses who look to move with the times should invest in an access control system with open APIs, that is based in the cloud and which integrates with other smart office technology. They should focus on designing a system that is customisable to their employees’ needs and which removes barriers to productivity.

Final Thoughts
Looking to upgrade to better access control? If you’re concerned about the reliability and strength of your access points, now is the time to upgrade. Ignoring the attractive benefits modern access control has to offer your business could cause expensive security issues in the long run.
At Chris Lewis Group, we understand the convenience and peace of mind access control can offer your building and its occupants. Our installation experts are highly experienced in specifying, designing, installing and maintaining solutions that are designed to meet your needs precisely and effectively.
We also supply a range of upgrade packages, helping you to put a modern twist on your existing legacy technology, for greater efficiency, smoother operation and more secure entrances.












